- Property Variables Configuration
- PMUSER_PX_APP_ID
- PMUSER_PX_AUTH_TOKEN
- PMUSER_PX_COOKIE_SECRET
- PMUSER_PX_S2S_TIMEOUT
- PMUSER_PX_MODULE_ENABLED
- PMUSER_PX_MODULE_MODE
- PMUSER_PX_FIRST_PARTY_ENABLED
- PMUSER_PX_CUSTOM_LOGO
- PMUSER_PX_JS_REF
- PMUSER_PX_CSS_REF
- PMUSER_PX_SENSITIVE_ROUTES
- PMUSER_PX_ENFORCER_DIR
- PMUSER_PX_SHARED_SECRET
- Placeholder Variables
- PMUSER_PX_FROM_AKAM
- PMUSER_PX_CHECK_ROUTE
- PMUSER_PX_COOKIE_V2
- PMUSER_PX_COOKIE_V2_U
- PMUSER_PX_COOKIE_V2_T
- PMUSER_PX_COOKIE_V2_V
- PMUSER_PX_COOKIE_V2_H
- PMUSER_PX_COOKIE_V2_UA
- PMUSER_PX_COOKIE_V2_HMAC_PASS
- PMUSER_PX_COOKIE_V2_HMAC_BLOCK
- PMUSER_PX_REQUEST_ID
Configuration
The initial configuration is determined during the installation process.
Once the Enforcer is installed, you can change its configuration through the Akamai Property Editor. Below you will find a description of all the defined Property Variables for the ESI Enforcer.
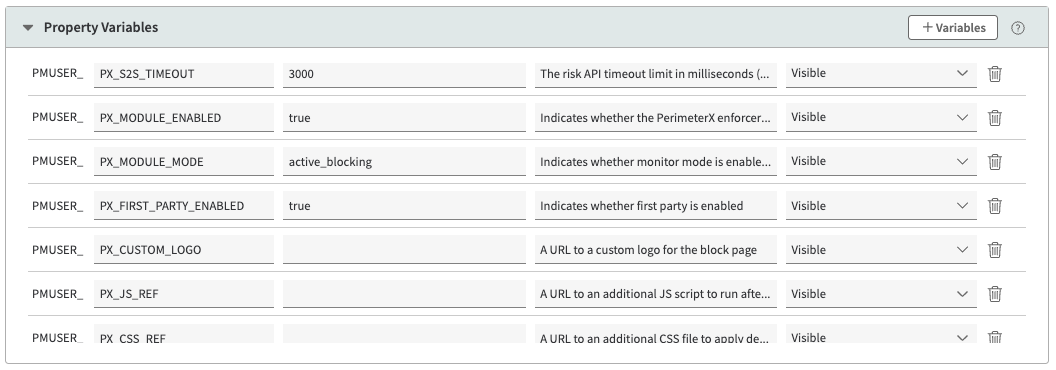
Property Variables Configuration
The following variables should be configured according to your Akamai ESI Enforcer setup.
PMUSER_PX_APP_ID
The app id.
Default Value: N/A
Visibility: Visible
PMUSER_PX_AUTH_TOKEN
The authentication token for the Risk API.
Default Value: N/A
Visibility: Hidden
PMUSER_PX_COOKIE_SECRET
The hash key for the cookie HMAC.
Default Value: N/A
Visibility: Hidden
PMUSER_PX_S2S_TIMEOUT
The risk API timeout limit in milliseconds. (Note: needs to be updated in risk_request.esi file as well!)
Default Value: 3000
Visibility: Visible
PMUSER_PX_MODULE_ENABLED
Indicates whether the enforcer is enabled.
Possible Values: true / false
Default Value: true
Visibility: Visible
PMUSER_PX_MODULE_MODE
Indicates whether monitor mode is enabled on the enforcer.
Possible Values: monitor / active_blocking
Default Value: monitor
Visibility: Visible
PMUSER_PX_FIRST_PARTY_ENABLED
Indicates whether first party is enabled.
Possible Values: true / false
Default Value: true
Visibility: Visible
PMUSER_PX_CUSTOM_LOGO
A URL to a custom logo for the block page. Max height: 150px, width: auto.
Default Value: Empty
Visibility: Visible
PMUSER_PX_JS_REF
A URL to an additional JS script to run after the default JS scripts on the block page.
Default Value: Empty
Visibility: Visible
PMUSER_PX_CSS_REF
A URL to an additional CSS file to apply design to the block page.
Default Value: Empty
Visibility: Visible
PMUSER_PX_SENSITIVE_ROUTES
Regex (PCRE) for sensitive routes. All requests whose paths match this regex will be considered sensitive, and a Risk API call will be made regardless of any cookies on the request.
Default Value: Empty
Example Value: ^(/login.*)|(/sign-in)$
Visibility: Visible
PMUSER_PX_ENFORCER_DIR
The root directory of the enforcer ESI files in NetStorage. Note: Must end with a trailing slash.
Default Value: /px_enforcer/
Visibility: Visible
PMUSER_PX_SHARED_SECRET
Security feature to validate if the route back from post request domain is valid (safeguards against requests trying to bypass the enforcer).
Default Value: N/A
Visibility: Hidden
Placeholder Variables
The following variables should be configured in the Akamai Property and left blank.
PMUSER_PX_FROM_AKAM
Placeholder for the extracted security header.
Visibility: Hidden
PMUSER_PX_CHECK_ROUTE
Placeholder for checking route back from post forwarded domain.
Visibility: Hidden
PMUSER_PX_COOKIE_V2
Placeholder for _px2 cookie from the request.
Visibility: Visible
PMUSER_PX_COOKIE_V2_U
Placeholder for ‘u’ field as extracted from _px2 cookie.
Visibility: Visible
PMUSER_PX_COOKIE_V2_T
Placeholder for t’ field as extracted from _px2 cookie.
Visibility: Visible
PMUSER_PX_COOKIE_V2_V
Placeholder for ‘v’ field as extracted from _px2 cookie.
Visibility: Visible
PMUSER_PX_COOKIE_V2_H
Placeholder for ‘h’ field as extracted from _px2 cookie.
Visibility: Visible
PMUSER_PX_COOKIE_V2_UA
Placeholder for user-agent header that arrived in the request.
Visibility: Visible
PMUSER_PX_COOKIE_V2_HMAC_PASS
Placeholder for valid passing cookie hmac format.
Visibility: Visible
PMUSER_PX_COOKIE_V2_HMAC_BLOCK
Placeholder for valid blocking cookie hmac format.
Visibility: Visible
PMUSER_PX_REQUEST_ID
Placeholder for request ID.
Visibility: Visible