HUMAN Plugin Configuration
Configuration
The HUMAN Lua Module configuration is in the following location:
/usr/local/lib/lua/px/pxconfig.lua
- The HUMAN Application ID / AppId and HUMAN Token / Auth Token / Authorization Token can be found in the Portal, under Applications.
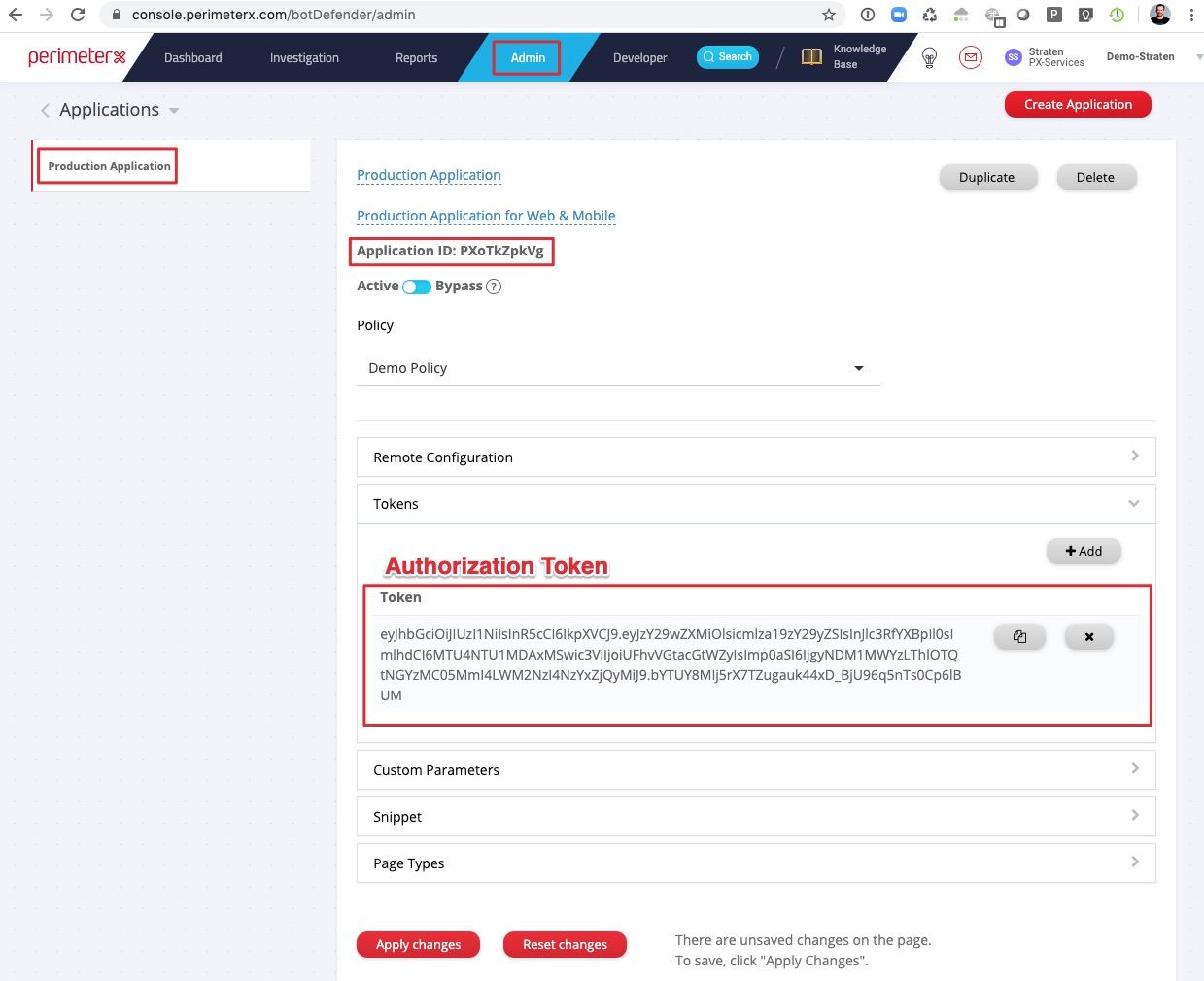
- HUMAN Cookie Encryption Key / Risk Cookie can be found in the portal, under Policies.
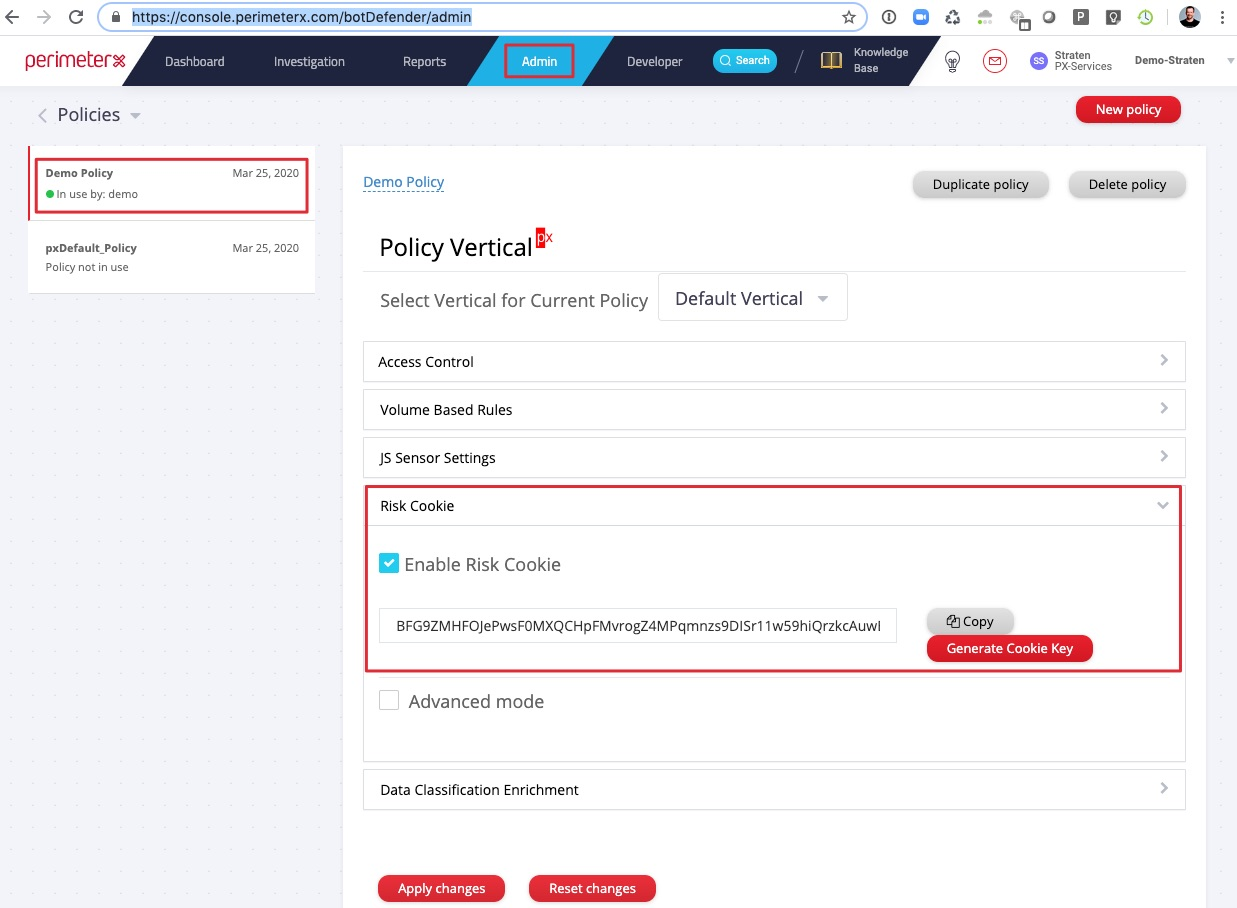
__NOTE: The Policy from where the Cookie Encryption Key is taken must correspond with the Application from where the Application ID / AppId and HUMAN Token / Auth Token __
Optional Configurations
PII (Personally Identifiable Information) Anonymization
Personally Identifiable Information (PII) is information that can be used on its own or with other information to identify a single person, or to identify an individual in context.
It is important for us to keep personal private information out of our servers. Therefore, by default, we do not send the request body and cookies to HUMAN backend servers; communication is based on header data.
PII is not a recommended setting. If PII is essential for your organization, contact HUMAN Support.
When PII is enabled, HUMAN does not store a client’s full IP information (client IP, HTTP headers). In IPv4, this is done by zeroing 4th IP octet (for example, the IP 1.2.3.4 will be stored as 1.2.3.0). In IPv6 this is done by zeroing the last four (4) octets (for example, the IP 1:2:3:4:1:2:3:4 will be stored as 1:2:3:4:1:2:3:0). Removing the IP’s last octet can result small reduction of detection capability, usually for the models and signatures that are based on IPs.
Monitor / Block Mode Configuration
By default, the HUMAN plugin is set to monitor mode.
_M.block_enabled = false
Adding the _ M.block_enabled flag and setting it to true in the pxconfig.lua file activates the module to enforce blocking. This means the HUMAN Module blocks requests that exceed the block score threshold. If a request receives a risk score that is equal to or greater than the block score, a block page is displayed.
Debug Mode
Enables debug logging mode.
Default: false (disabled)
_M.px_debug = true
When Enabled, HUMAN debug messages should be in the following template:
- For debug messages -
[PerimeterX - DEBUG] [APP_ID] - MESSAGE - For error messages -
[PerimeterX - ERROR] [APP_ID] - MESSAGE
Valid request flow example:
Allowlist
Allowing (bypassing enforcement) is configured in the pxconfig.lua file.
Several filters can be configured:
Filter Sensitive Headers
A list of sensitive headers configured to prevent specific headers from being sent to HUMAN servers (headers in lowercase). Filtering cookie headers for privacy is set by default, and can be overridden on the pxConfig variable.
Default: cookie, cookies
Example:
Remote Configurations
Allows the module to periodically pull configurations from HUMAN services. When enabled, the configuration can be changed dynamically via HUMAN Portal
Default: false
File: pxconfig.lua
Example:
Enabled Routes
Allows you to define a set of routes on which the plugin will be active. An empty list sets all routes in the application as active.
Default: Empty list (all routes are active)
Example:
Sensitive Routes
A list of route prefixes and suffixes. The HUMAN module always matches the request URI with the prefixes list and suffixes list. When there is a match, the HUMAN module creates a server-to-server call, even when the cookie is valid and the risk score is low.
Default: Empty list
Example:
API Timeout Milliseconds
API Timeout in milliseconds (float) to wait for the HUMAN server API response. The API is called when a risk cookie does not exist, is expired, or is invalid. If the timeout is reached before a response is received, the module will pass the client request.
Default: 1000
Example:
Customize Default Block Page
The HUMAN default block page can be modified by injecting custom CSS, JavaScript and a custom logo to the block page.
Default: nil
Example:
Redirect to a Custom Block Page URL
Customizes the block page to meet branding and message requirements by specifying the URL of the block page HTML file. The page can also implement CAPTCHA.
Default: nil
Example:
This URI is allowed automatically under _M.Whitelist['uri_full'] to avoid infinite redirects.
Redirect on Custom URL
The _M.redirect_on_custom_url boolean flag to redirect users to a block page.
Default: false
Example:
By default, when a user exceeds the blocking threshold and blocking is enabled, the user is redirected to the block page defined by the _M.custom_block_url variable. The defined block page displays a 307 (Temporary Redirect) HTTP Response Code.
When the flag is set to false, a 403 (Unauthorized) HTTP Response Code is displayed on the blocked page URL.
Setting the flag to true (enabling redirects) results in the following URL upon blocking:
Setting the flag to false does not require the block page to include any of the examples below, as they are injected into the blocking page via the HUMAN NGINX Module.
The URL variable should be built with the URL-encoded query parameters (of the original request) with both the original path and variables base64-encoded (to avoid collisions with block page query params).
Custom Block Pages Requirements
As of version 4.0, Captcha logic is handled through the JavaScript snippet and not through the enforcer.
Users who have Custom Block Pages must include the new script tag and a new div in the .html block page. For implementation instructions refer to the appropriate links below:
Redirect to Referer
Indicates whether the user is redirected from the challenge page to the referrer page after successfully solving the challenge.
Default: false
Example:
Additional Activity Handler
An additional activity handler is added by setting _M.additional_activity_handler with a user defined function in the ‘pxconfig.lua’ file.
Default: Activity is sent to HUMAN as controlled by ‘pxconfig.lua’.
Example:
Enrich Custom Parameters
With the enrich_custom_params function you can add up to 10 custom parameters to be sent back to HUMAN servers. When set, the function is called before setting the payload on every request to HUMAN servers. The parameters should be passed according to the correct order (1-10). You must return the px_cusom_params object at the end of the function.
Default: nil
Example:
Changing the Minimum Score for Blocking
This value should not be changed from the default of 100 unless advised by HUMAN.
Default blocking value: 100
Example:
First-Party Prefix
Allows you to define a custom prefix for First-Party routes.
Default: nil
Example:
To define the First-Party Prefix
-
In your
pxconfig.luafile, set the_M.first_party_prefixproperty to the desired prefix value. For example: -
Open the HUMAN Console.
-
Go to
Admin->Applications. -
Open the
Snippetsection. ActivateFirst-Party(if not in First-Party already), and clickEditnext to the Copy Snippet button. -
In the pop-up that opens there are two routes beginning with
/<appId without PX>. Copy both routes to a side document to use in the next steps. -
Click
Advanced Configuration. -
Under Sensor, copy the first route from step 5 and add the prefix you added in step 1 to the beginning of of the route.
For example:/resources/<appId without PX>/init.js -
Under Server copy the second route from step 5 and the prefix you added in step 1 to the beginning of the route.
For example:/resources/<appId without PX>/xhr -
Click
Save Changes. -
Click
Copy Snippetand update the JS Sensor snippet of your site with the updated one.
Advanced Blocking Response Support
Enables/disables support for Advanced Blocking Response.
Default: true (enabled)
Example:
Proxy Support
Sets a proxy server for all the enforcer’s outgoing calls.
Requires
lua-resty-httpversion 0.12 and up.
Default: nil
Example:
Proxy Authorization
If proxy support is enabled, allows you to set a proxy authorization header.
Requires
lua-resty-httpversion 0.12 and up.
Default: nil
Example:
Custom Cookie Header
When set, this property specifies a header name that will be used to extract the HUMAN cookie from, instead of the Cookie header.
Using a custom cookie header requires client-side integration to be done as well. Please refer to the relevant docs for details.
Default: nil
Example:
Bypass Monitor Mode Header
When set, allows you to test the blocking flow of an enforcer, while in monitoring mode. When the enforcer receives a request that has this configured header name with the value of 1, it will behave as though it is in active blocking mode. For instance, requests with this header and bad user-agents (e.g., PhantomJS/1.0) will return with a block page.
Default: nil