Complete Example
This is a complete example of Envoy and HUMAN Callout Enforcer.
We have the following test setup:
- Envoy listens on 10.0.0.1:8080
- HUMAN Callout Enforcer is on 10.0.0.1:50051
- A protected web server is
www.envoyproxy.io:443
- Complete Envoy configuration (
envoy.yamlfile):
1 static_resources: 2 listeners: 3 - name: listener_0 4 address: 5 socket_address: 6 protocol: TCP 7 address: 0.0.0.0 8 port_value: 8080 9 filter_chains: 10 - filters: 11 - name: envoy.filters.network.http_connection_manager 12 typed_config: 13 "@type": type.googleapis.com/envoy.extensions.filters.network.http_connection_manager.v3.HttpConnectionManager 14 scheme_header_transformation: 15 scheme_to_overwrite: https 16 stat_prefix: ingress_http 17 route_config: 18 name: local_route 19 virtual_hosts: 20 - name: local_service 21 domains: ["*"] 22 routes: 23 - match: 24 prefix: "/" 25 route: 26 host_rewrite_literal: www.envoyproxy.io 27 cluster: service_envoyproxy_io 28 http_filters: 29 - name: envoy.filters.http.ext_proc 30 typed_config: 31 "@type": type.googleapis.com/envoy.extensions.filters.http.ext_proc.v3.ExternalProcessor 32 grpc_service: 33 envoy_grpc: 34 cluster_name: px_callout_cluster 35 timeout: 3s 36 failure_mode_allow: false 37 allow_mode_override: true 38 message_timeout: 3s 39 processing_mode: 40 request_header_mode: "SEND" 41 response_header_mode: "SEND" 42 request_body_mode: "NONE" 43 response_body_mode: "NONE" 44 request_trailer_mode: "SKIP" 45 response_trailer_mode: "SKIP" 46 47 - name: envoy.filters.http.router 48 typed_config: 49 "@type": type.googleapis.com/envoy.extensions.filters.http.router.v3.Router 50 clusters: 51 - name: service_envoyproxy_io 52 connect_timeout: 30s 53 type: LOGICAL_DNS 54 dns_lookup_family: V4_ONLY 55 lb_policy: ROUND_ROBIN 56 load_assignment: 57 cluster_name: service_envoyproxy_io 58 endpoints: 59 - lb_endpoints: 60 - endpoint: 61 address: 62 socket_address: 63 address: www.envoyproxy.io 64 port_value: 443 65 transport_socket: 66 name: envoy.transport_sockets.tls 67 typed_config: 68 "@type": type.googleapis.com/envoy.extensions.transport_sockets.tls.v3.UpstreamTlsContext 69 sni: www.envoyproxy.io 70 71 - name: px_callout_cluster 72 type: STRICT_DNS 73 lb_policy: ROUND_ROBIN 74 connect_timeout: 1s 75 http2_protocol_options: {} 76 load_assignment: 77 cluster_name: px_callout_cluster 78 endpoints: 79 - lb_endpoints: 80 - endpoint: 81 address: 82 socket_address: 83 address: 10.0.0.2 84 port_value: 50051 85 health_checks: 86 - timeout: 1s 87 interval: 1s 88 unhealthy_threshold: 1 89 healthy_threshold: 1 90 reuse_connection: true 91 tls_options: 92 alpn_protocols: ["h2"] 93 grpc_health_check: 94 service_name: health_check 95 transport_socket: 96 name: envoy.transport_sockets.tls 97 typed_config: 98 "@type": type.googleapis.com/envoy.extensions.transport_sockets.tls.v3.UpstreamTlsContext
- Run Envoy:
1 docker run --rm \ 2 -p 8080:8080 \ 3 --mount type=bind,source="$(pwd)"/envoy.yaml,target=/etc/envoy/envoy.yaml \ 4 --config-path /etc/envoy/envoy.yaml \ 5 -l info \ 6 envoyproxy/envoy:v1.29-latest
- An example of HUMAN Callout Enforcer configuration (
pxconf.jsonfile):
1 { 2 "px_appId": "--REPLACE--", 3 "px_cookie_secret": "--REPLACE--", 4 "px_auth_token": "--REPLACE--", 5 "px_whitelist_uri_full": ["/test", "/abc"], 6 "px_block_enabled": true, 7 "px_score_header_enabled": true, 8 "px_score_header_name": "x-px-score" 9 }
- Run HUMAN Callout Enforcer:
1 docker run --rm \ 2 -p 50051:50051 3 --mount type=bind,source="$(pwd)"/pxconf.json,target=/etc/pxconf.json,readonly \ 4 perimeterx/px-callout-enforcer:latest
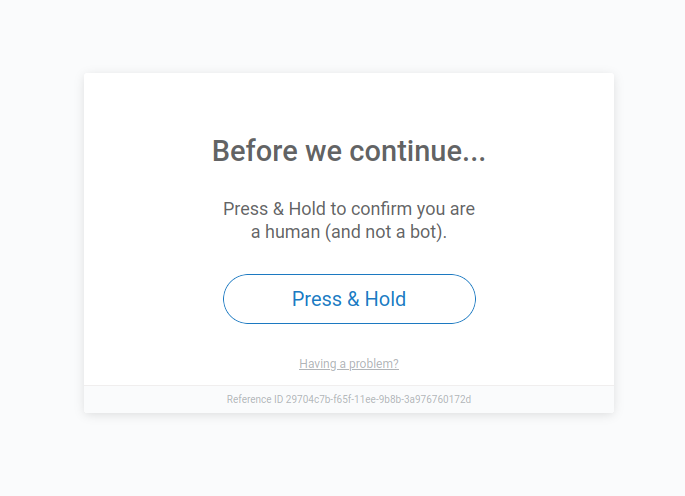
- To test the new setup, open
http://10.0.0.1:8080/address in a web browser (enable “PhantomJS” UA), you should see HUMAN Captcha page: