Install the Azure Front Door Enforcer
If your organization uses Azure Front Door, you can use HUMAN’s Azure Front Door Enforcer to protect against malicious behavior, which dictates how traffic should be handled per your organization’s standards. The Azure Enforcer combines Azure’s Front Door CDN caching functionality with the Azure Function App’s ability to run serverless code in the cloud.
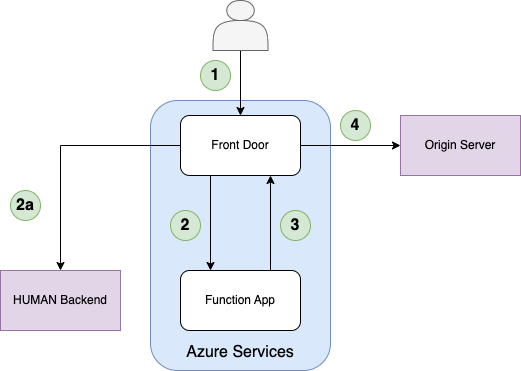
- The client sends a request to Azure Front Door.
- Front Door sends the incoming request to the Function App origin group.
- Reduces Function App invocations in the case of First Party requests.
- If the Enforcer in the Function App passes the request, the Azure Function proxies the request back to the same Front Door domain.
- If not found in the cache, the Front Door Rule Set sends the request to the origin server.
You can learn how to install the Azure Front Door Enforcer with this article.
This process only works if you do not have an existing Enforcer integrated with your application. If you do, see our article on manual installation.
Prerequisites
- An Azure subscription with at least a Contributor role and the following providers:
Microsoft.Cdn(for Front Door)Microsoft.Storage(for Storage Accounts)Microsoft.Sites(for App Service)Microsoft.Resources(for Resource Groups)Microsoft.Web(for Function Apps)
- A supported Azure app service plan on the same region you want to deploy your Enforcer to. The supported plans are:
- Basic
- Standard
- Premium
- Isolated
- An Azure resource group within the relevant subscription.
- Depending on your preferred deployment method, the following tools:
- Docker method:
- Docker. See how to install Docker with their documentation.
- Script method:
- Node.js 20.x or later and npm 10.x or later. See how to install both with npm’s documentation.
- Git CLI. You can download it directly from Git.
- GNU Wget. See how to install with their documentation.
- Docker method:
Create a Service Principal Client Secret
The Enforcer requires a client secret from a Service Principal. If you have an existing one, you can use it to create a secret. If you don’t have one, you can follow the steps to create a new one.
Create a new Service Principal
- Follow the steps in Microsoft’s help article section Register an application with Microsoft Entra ID and create a service principal. While doing so, make sure that you do the following for the specified fields:
- Name: Choose a descriptive name (e.g. “Human Security Enforcer Deploy Tool”)
- Supported account types: Select “Accounts in this organizational directory only”
- Redirect URI: Leave blank
- After registering your Service Principal, note the Client (Application) ID and Tenant (Directory) ID. You’ll need these values later.
Create a client secret
- Follow the steps in Microsoft’s help article section Option 3: Create a new client secret.
- After you create the client secret, be sure to copy and save it in a secure place. You will not be shown the secret again.
Download the Enforcer configuration file
The Enforcer configuration file, enforcerConfig.json, has important information about your HUMAN account such as your Application ID or server token that the Enforcer uses to work with your application. If you don’t have one already, you need to download this file from the HUMAN console.
- Navigate to Platform Settings > Configurations > Enforcers.
- Click the Enforcer that you’re currently updating.
- Click the download
 button to download
button to download enforcerConfig.json. - Save the file in a directory that you’ll remember, such as
/deploy.
Run the Deploy Tool
You can run the Deploy Tool with either of the following methods:
Docker method
Note for Windows users
Windows users also need to complete additional setup for Docker:
- In your Windows search bar, search for and open “Turn Windows features on or off”.
- Find the Windows Hypervisor Platform feature and enable it.
- Click OK to save your changes.
- Open Windows PowerShell as an Administrator.
- Copy and paste in
C:\Windows\System32\wsl.exe --update --web-download, then hit Enter.
- Navigate to the directory where you created
enforcerConfig.json. Based on our example from above, this would be the/deploydirectory. - Run the deploy tool with the following:
Script method
- Navigate to the directory where you created
enforcerConfig.json. Based on our example from above, this would be the/deploydirectory. - Pull the HUMAN Deploy Tool zip from Google Artifact Registry using:
- Unzip
cdn-enforcer-deploy-tool.zipto the same directory you savedenforcerConfig.jsonin. - Run the tool by opening the appropriate script for your system:
- Windows:
cdn-enforcer-deploy-tool.bat - Mac or Linux:
cdn-enforcer-deploy-tool.command
- Windows:
Deploy the Enforcer
- When prompted, select the Azure Front Door platform and hit Enter.
- Continue to follow the steps that appear to complete your deployment.
- When you finish the setup, confirm that the displayed details are correct, then enter
yto deploy the Enforcer.