Dashboard SSO - OneLogin
By default, HUMAN uses standard authentication to grant all HUMAN Dashboard users a simple, secure login experience. However, if your organization uses single sign-on (SSO) to manage internal user accounts across multiple tools, you can configure your SSO platform to access the HUMAN Dashboard. This allows your users to log in to the HUMAN Dashboard with their SSO credentials and gives your organization greater control over user access and permissions.
This guide explains how to configure SSO access through OneLogin. We also offer an SSO integration with Okta.
Requirements
Before you begin, you must notify HUMAN that you want to enable OneLogin SSO access for your organization. A HUMAN representative will provide you with a set of unique identity credentials that you’ll need to provide when you configure your OneLogin instance.
You’ll also need a OneLogin account with Super User permissions.
Configure OneLogin
After you’ve obtained the required credentials from HUMAN, you can integrate your OneLogin instance with the HUMAN Dashboard. To configure OneLogin, complete the following steps:
- Sign in to your OneLogin portal, then navigate to Administration > Applications.
- Select Add App.
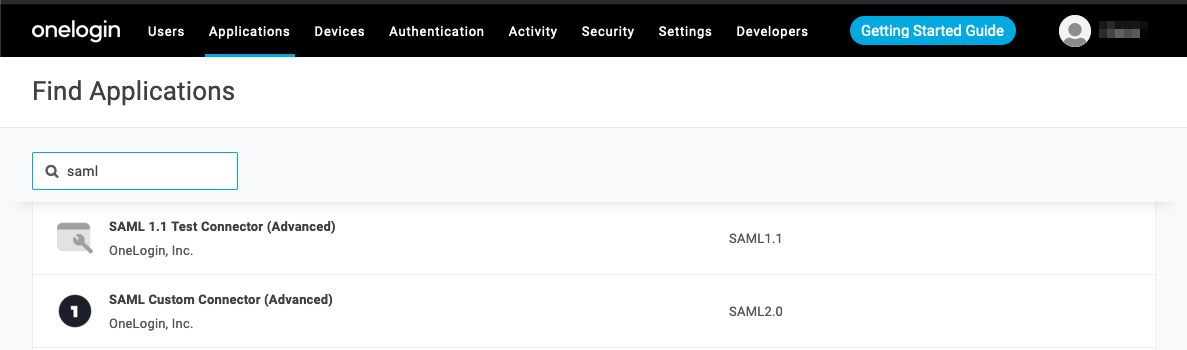
- On the Find Applications menu, search for “saml”; then choose SAML Custom Connector (Advanced) (SAML2.0).
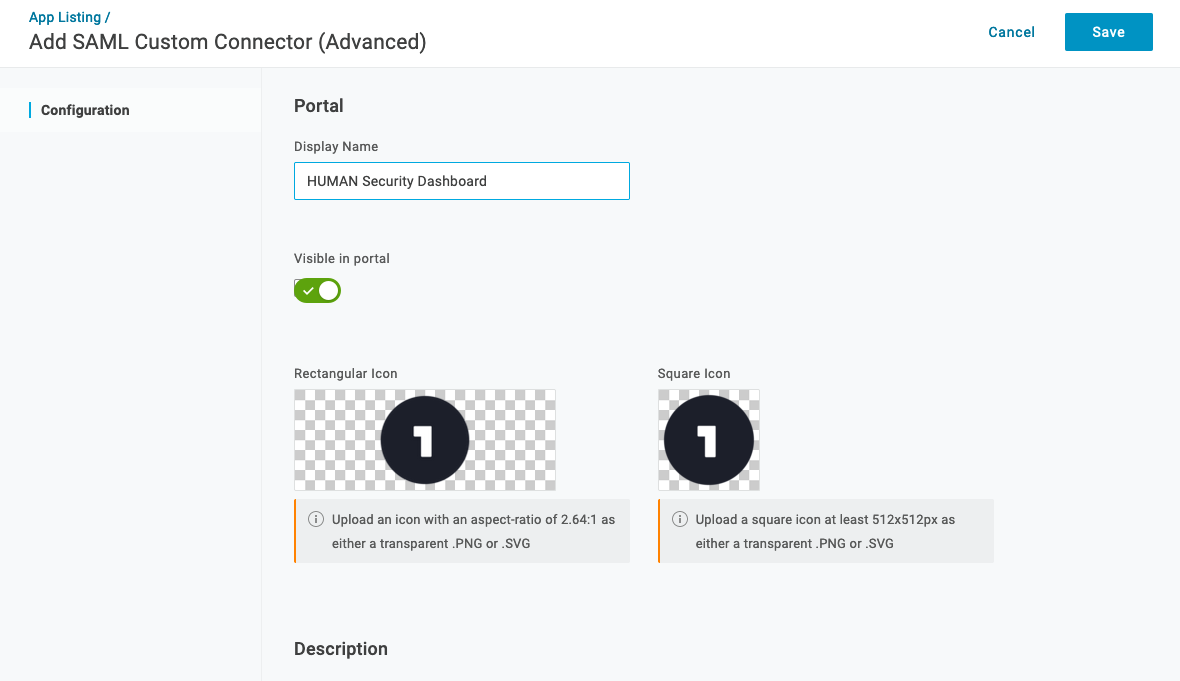
- On the Configuration tab of the Add SAML Custom Connector (Advanced) menu, enter “HUMAN Security Dashboard” in the
Display Namefield. You can also upload an icon for your connector, but it’s not required. - Select Save.
-
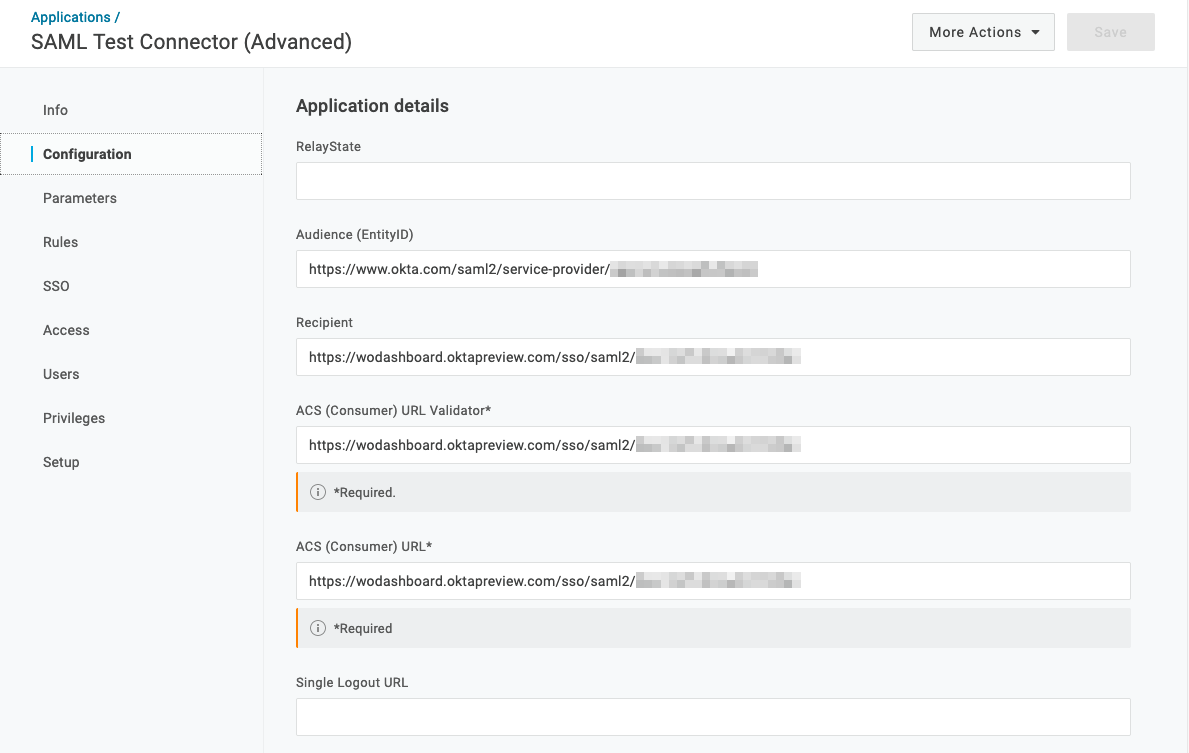
On the Configurations tab of the SAML Test Connector (Advanced) menu, set the
Audience (EntityID),Recipient,ACS (Consumer) URL Validator, andACS (Consumer) URLfields to the values that HUMAN provided you with. -
On the same tab, verify that each field is set to the following values:
SAML not valid before= 3SAML not valid on or after= 3SAML initiator= OneLoginSAML nameID format= EmailSAML issuer type= GenericSAML signature element= BothEncrypt assertion= No (box unchecked)SAML encryption method= AES-128-CBCSend NameID Format in SLO Request= No (box unchecked)Generate AttributeValue tag for empty values= No (box unchecked)SAML sessionNotOnOrAfter= 1440Sign SLO Request= No (box unchecked)Sign SLO Response= No (box unchecked)
-
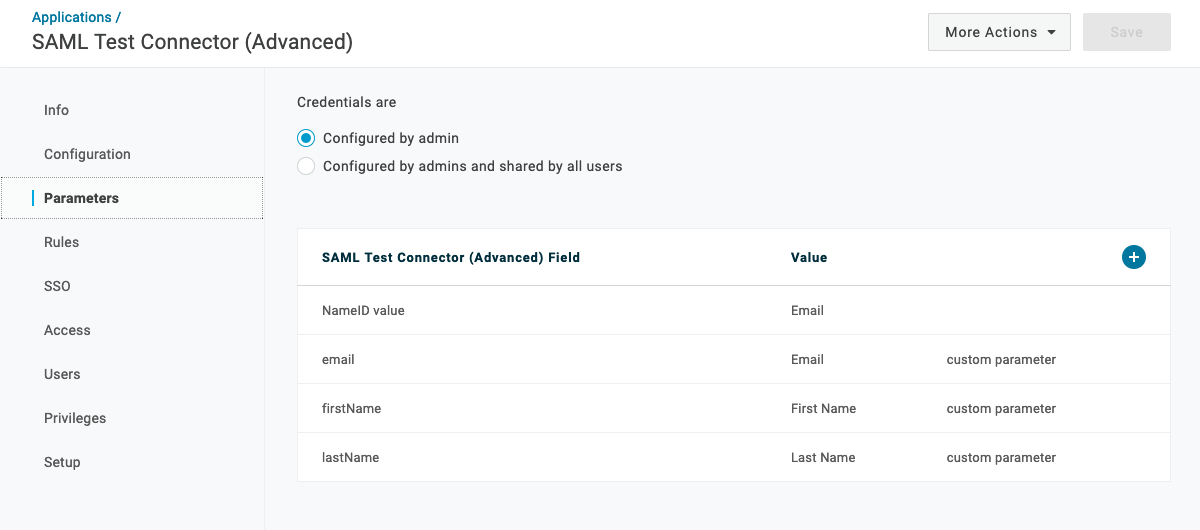
On the Parameters tab, set the
Credentials areoption to Configured by admin. -
On the same tab, create three custom parameters called
email,firstName, andlastName. As you create each parameter, ensure that theInclude in SAML assertioncheckbox is selected. Then verify that each parameter is set to the following values:NameID value= Emailemail= EmailfirstName= First NamelastName= Last Name
-
On the SSO tab, select SHA-256 from the SAML Signature Algorithm drop-down menu.
-
Select Save.
- After you’ve created your connector, navigate back to the SSO tab.
TheIssuer URLandSAML 2.0 Endpoint (HTTP)fields each contain a URL value. - Send these two URLs to a HUMAN representative so we can finalize your OneLogin integration.
After this process is complete, you’ll be able to manage your organization’s SSO access to the HUMAN Dashboard.